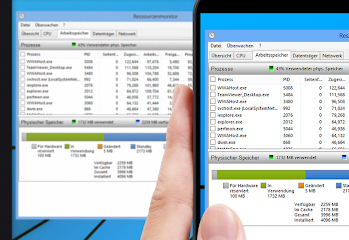
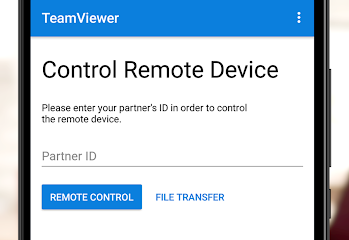
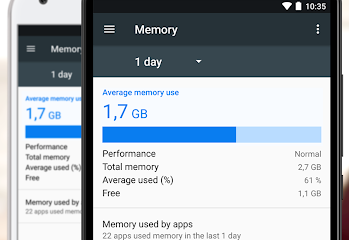
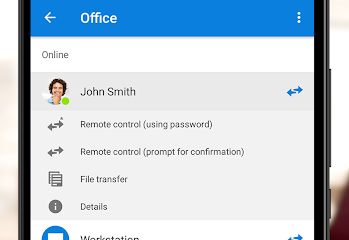
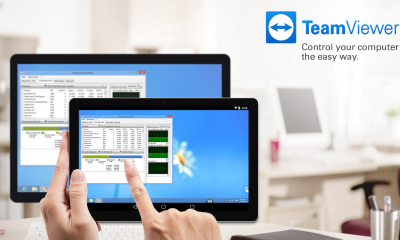
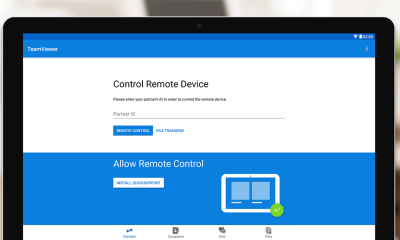
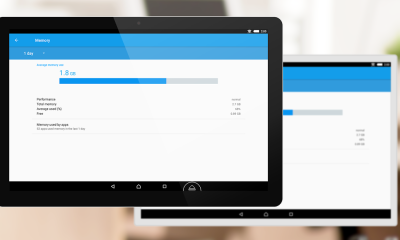
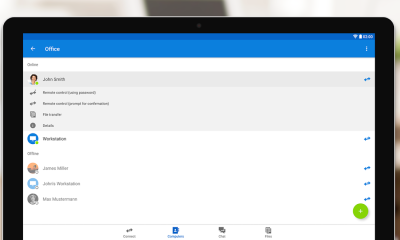
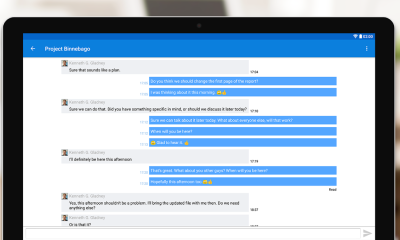
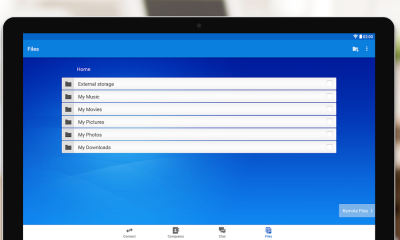
Get TeamViewer for Remote Control
All trademarks belong to their respective owners.
Sponsored links

Get the TeamViewer for Remote Control
Astrosnout.com does not claim ownership of this content.
Astrosnout.com does not claim ownership of this content.
FAQ
New on Blog
-
- Ryan Gutierrez
- 09 Feb 2026

-
- Ryan Gutierrez
- 09 Feb 2026

-
- Kayla Cruz
- 23 Jan 2026

-
- Kayla Cruz
- 23 Jan 2026

-
- Kayla Cruz
- 23 Jan 2026

-
- Kayla Cruz
- 09 Jan 2026

Recommended
-
 Limbus Company Overview of Limbus Company As an experienced gamer who has witnessed the evolution of gaming trends over the years, encountering L Read full review
Limbus Company Overview of Limbus Company As an experienced gamer who has witnessed the evolution of gaming trends over the years, encountering L Read full review -
 Wicked: For Good An In-Depth Journey Through Wicked: For GoodI recently had the pleasure of immersing myself in Wicked: For Good, a film that dives Read full review
Wicked: For Good An In-Depth Journey Through Wicked: For GoodI recently had the pleasure of immersing myself in Wicked: For Good, a film that dives Read full review -
 Little Nightmares An Immersive Dive into Little Nightmares Stepping into the eerie world of Little Nightmares is like entering a surreal dreamscape Read full review
Little Nightmares An Immersive Dive into Little Nightmares Stepping into the eerie world of Little Nightmares is like entering a surreal dreamscape Read full review -
 The Grinch An Unconventional Take on a Timeless Tale In the realm of holiday classics, The Grinch stands out as an oddly endearing figure wh Read full review
The Grinch An Unconventional Take on a Timeless Tale In the realm of holiday classics, The Grinch stands out as an oddly endearing figure wh Read full review -
 Home Alone A Timeless Blend of Comedy and Heart Home Alone remains a cinematic gem that has captivated audiences for decades. As an experien Read full review
Home Alone A Timeless Blend of Comedy and Heart Home Alone remains a cinematic gem that has captivated audiences for decades. As an experien Read full review -
 How the Grinch Stole Christmas Unwrapping the Magic and Mischief of How the Grinch Stole Christmas Stepping into the whimsical world of How the Grinch Stole Chr Read full review
How the Grinch Stole Christmas Unwrapping the Magic and Mischief of How the Grinch Stole Christmas Stepping into the whimsical world of How the Grinch Stole Chr Read full review